
The Last Mile in Performing Privacy Impact Assessments Effectively
Reyes Tacandong & Co. (RT&Co.) is one of the top Philippine professional firms which pioneered the data privacy and protection services in 2017.
Five years since the release of the Implementing Rules and Regulations (IRR) and Commission’s privacy toolkit, the data privacy implementers—Data Protection Officers (DPOs), Compliance Officers for Privacy (COPs), Assessors and Auditors—are already mostly familiar with the Privacy Impact Assessment (PIA) tools and templates prescribed by the National Privacy Commission (NPC). No doubt, these tools have been important in jump starting the conduct of PIAs, especially during the early years of data privacy implementation.
Many companies have since learned that beyond use of the handy but generic tools that the NPC has handed down, PIAs are ultimately bespoke and that understanding and accommodating the organizational context in privacy risk reviews is essential. In RT&Co., we call this the “last mile” challenge in privacy impact assessments.
Reyes Tacandong & Co. (RT&Co.) is one of the top Philippine professional firms which pioneered the data privacy and protection services in 2017. Since then, our people have dedicated a lot of time lot time expanding the NPC toolkit to incorporate our very own approach in tackling the last mile challenge and in ensuring that the sometimes intricate but always specific requirements of data privacy protection of our clients are met.
What differentiates our methodology with the National Privacy Commission’s privacy toolkit when conducting Privacy Impact Assessment?
The NPC’s privacy principles and toolkit underpins our PIA methodology. It builds on the processes and activities envisioned by the NPC—from conducting the threshold analysis to privacy governance and data management analysis, completing the privacy impact analysis, creating the data flow diagram and data inventory, performing the technical security measures assessment, and, finally, crafting the privacy risk assessment and treatment plan (see Figure 1: RT&Co. PIA Approach and Methodology).
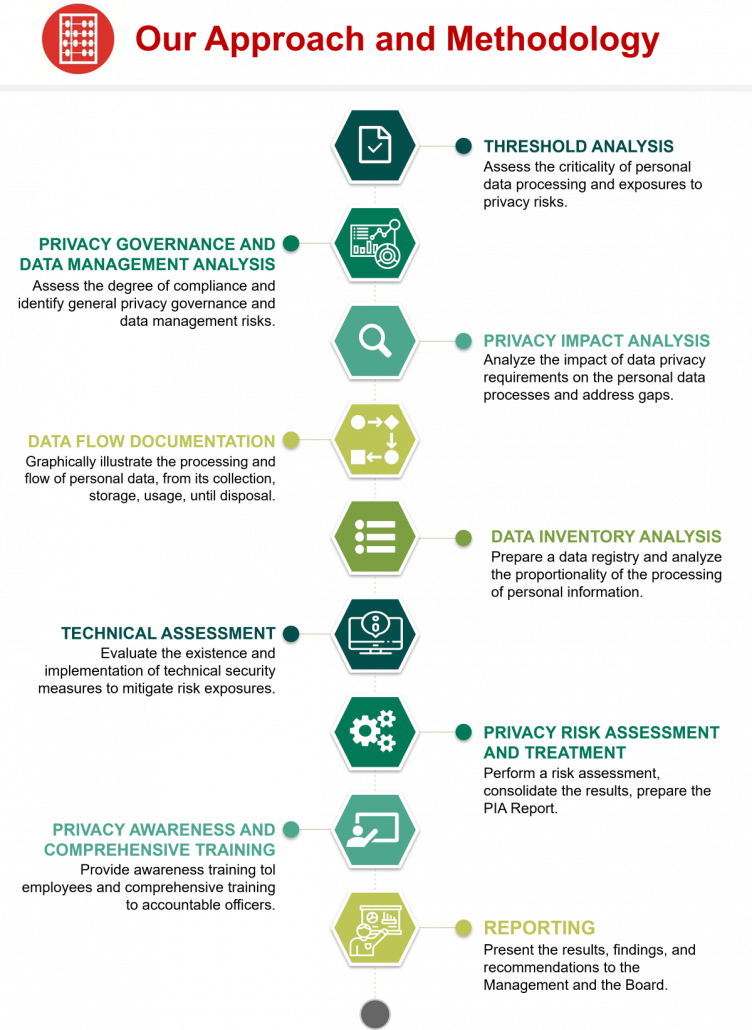
Figure 1: RT&Co. PIA Approach and Methodology
Over the years in the process of assisting clients that included top companies across diverse industries—from logistics to financial services, retail, and mining—we have encountered last mile hurdles to fully comply with the requirements of the law and realized that the last mile is often peculiar and unique for each company. In response, we took the standard NPC toolkit further by developing principles and approaches that aimed to account for the needs as well as the challenges that are unique to each client. Through our extended methodology, we could not only better understand the different data processing systems that are unique to each company, sector, and industry but also recommend a privacy protection program well suited for those unique circumstances.
What are the examples of last mile requirements?
In this section, we briefly present here the top four last mile challenges our Firm has encountered in assisting our clients.
1. How do we achieve clarity of roles between the different data privacy implementers: the DPO, the COPs, the DPS Owners, Process Owners and other Data Handlers?
The first of five pillars of privacy compliance is the appointment of DPO and designation of COP/s to assist the DPO. However, the NPC doesn’t tell us who the DPO or COP should be nor does it indicate specifically how the COP would support the DPO. To address this gap, we have ensured that our methodology allows us to obtain a comprehensive overview of the client’s whole work system in order for us to define the accountability of the DPO and COP as well as the extent of the latter’s support activities.
To achieve clarity of roles between the different data privacy implementers, we need to further distinguish the ownership of the data processing system (DPS) from the DPO and COP itself. Naturally, data processing activities rely on the core business processes of the company—therefore, the data belongs to the process owner, not the DPO nor the COP. Hence, before registering of any given DPS with the NPC, it is best practice to clearly specify the accountable DPS owner cum process owner. Clarity in the progression of the accountability from the DPO to the COPs and, ultimately, to the DPS and process owners is important to ensure that nothing falls between the cracks.
Our methodology ensures clarity in the accountability and ownership between various data privacy implementers:
- We assist in crafting the mechanics for compliance and performance monitoring of the different stakeholders of data privacy as well as help identify qualified people to become COP/s in the organization.
- We help identify personnel who are best suited to take on the role of a DPS owner consistent with the Company’s systems and organization and its process and data flows.
2. How do we get the right level of information and engagement across the organization?
One of the questions that our clients usually ask is: “Who is responsible for making sure that we protect the privacy of the information of our data subjects?” Risk management 101 has a ready answer: Everybody who touches the data is responsible! That said, the degree of responsibility of each individual obviously depends on the structure of the organization and the number of data touchpoints in his/her process. The DPO’s privacy team would need the support of the whole organization—starting from the Board of Directors and Senior Management down to the implementers coming from different business units and assurers (e.g., internal auditors and external assessors) to successfully and fully comply with the law requirements (See Figure 2: Organizational Support).
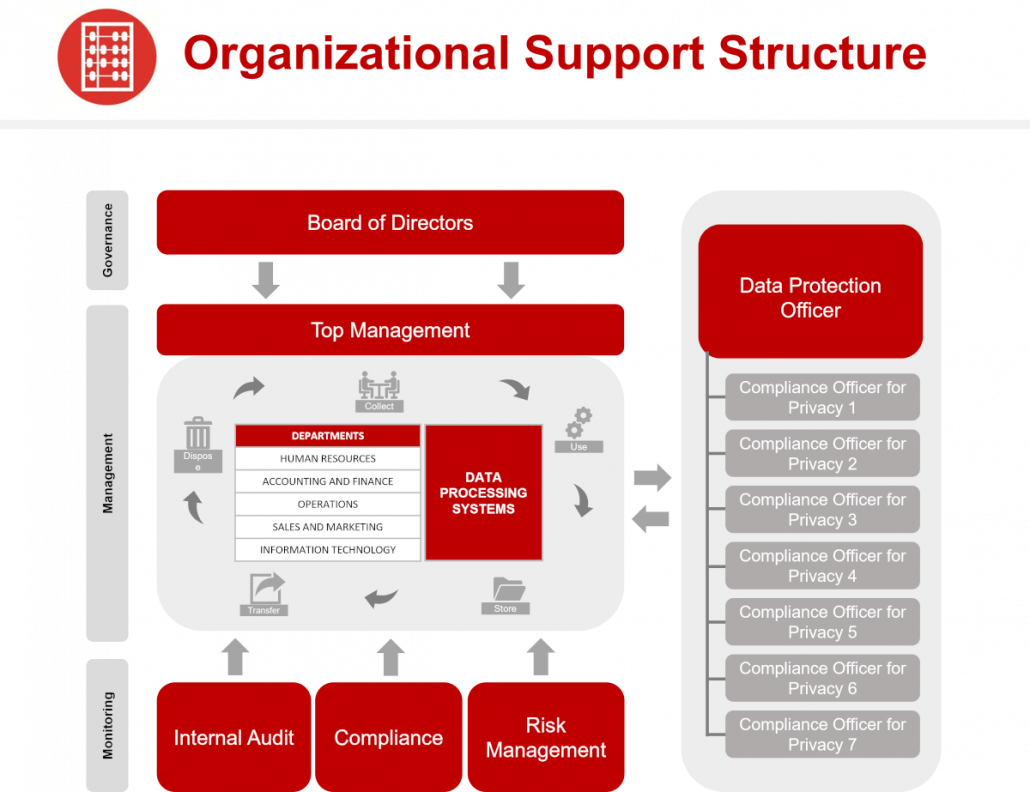
Figure 2: Organizational Support
The second question our clients would ask us is: “How do we make sure that all these people are fully informed about what needs to be done by the organization?”
The company has the responsibility to make sure that everybody is well-informed about data privacy so that they can perform their responsibilities well. This responsibility begins with the initial privacy impact assessments. Thus, privacy awareness training sessions are a key component to start off the privacy protection journey. It is meant to not just to inform the responsible individuals, but also to engage them.
Our awareness training sessions provide not only general information on data privacy to process owners and other data handlers but also encourage the growth of a culture of privacy awareness and respect for the rights of the data subjects. A culture of privacy awareness means that process owners embrace the importance of the different privacy principles, policies, procedures and guidelines defined in the data privacy management program to their respective business units. We also offer comprehensive training sessions to provide more detailed information to accountable privacy officers, equip them with the right knowledge and become familiar with their roles and responsibilities. After all, training and development is one way of effectively cultivating awareness and privacy culture in an organization.
3. How do we integrate and embed the right data privacy protection practices in an organization’s BAU?
To effectively embed and make data privacy protection practices operational, specific data protection activities required by the privacy principles should be integrated in the business processes or day-to-day operations. To achieve this, privacy by design is one effective approach in developing and implementing projects, programs, and processes that integrates into the latter’s design or structure safeguards that are necessary to protect and promote privacy, such as appropriate organizational, technical and physical measures. Also, our realization is that to successfully transform data privacy and protection practices as BAU, we must incorporate and highlight the roles of responsibilities in the job descriptions of the organization’s personnel—from top to bottom. Another effective way to transform data privacy as BAU is to create and establish a performance metrics which outline and highlight the key performance indicators and the success rate of the company’s data privacy practices.
Further, to address this last mile problem, we have designed our methodology to include the development of a privacy compliance dashboard using data visualization and data analytics software tools. The privacy compliance dashboard is meant to measure and monitor compliance with the privacy management program of the different stakeholders. Not only does our methodology ensure the accuracy and completeness of the data, but it also ensures that we deliver data that are clear and understandable so that our clients will be able to fully comprehend the information presented, get insights and use these insights in making relevant and impactful decisions.
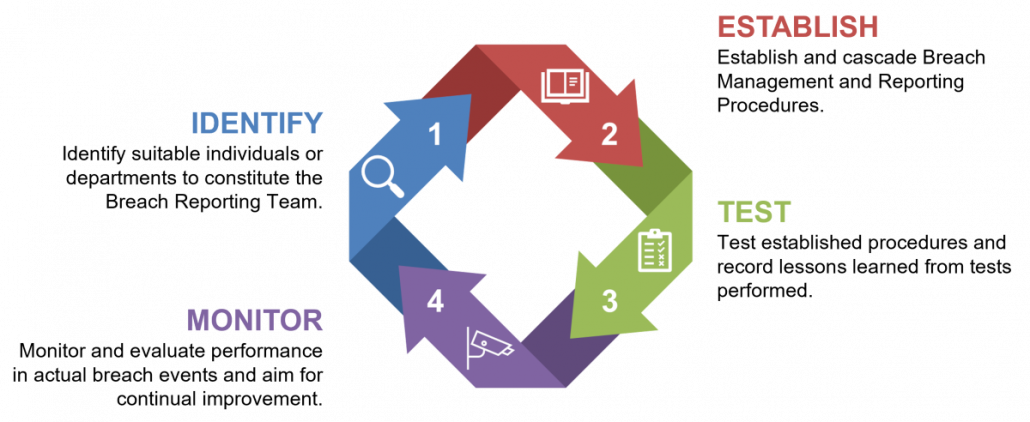
4. Data breach is not something that happens every day because we spend a lot of time and effort to prevent it. How do we keep people aware of what needs to be done in the unlikely event that it happens?
People need to always remember what to do in case of a data breach. Hence, the last pillar of privacy compliance “regularly exercise your breach and reporting procedure”. In assessing the organization’s preparedness for data breaches, we benchmark against the principles of business continuity planning.
Two important components in training sessions we provide are handling and reporting data breaches, and conducting data breach drills—both of which are highly crucial in crafting business contingency plans.
Most companies are in the race to accelerate their innovation and digital transformation programs in the emerging post-COVID business environment. In this race, an important guard rail that keeps you from getting off track is in prioritizing compliance with Data Privacy. There is no shortcut to success—after all, Rome was not built in a day.
Privacy compliance, itself, is a continuous journey that requires the active engagement of all stakeholders in an organization. The key to fully commit and achieve your digital transformation and privacy compliance goals is RT – Readiness for Transformation!

MARIA GABRIELLE ISABEL CRESPO
Associate for Advisory Services
[email protected]

ELIZER P. BETINOL
Senior Manager for Advisory Services
[email protected]

CAESAR V. PARLADE
Managing Partner for Advisory and Digital Transformation
[email protected]
Contact us today. We’ll schedule a complimentary assessment of your company.
Let RT&Co help your business. Send your request for a proposal of services here.
